Reverse Engineering
Assembly code for a 32-bit linux binary provided with 3 calling arguments. The arguments are passed in the stack when using the x32 calling convention. Follow the program to get the result.
Function Call: asm3(0xd73346ed,0xd48672ae,0xd3c8b139)
Assembly Code
<+0>: push ebp
<+1>: mov ebp,esp
<+3>: xor eax,eax
<+5>: mov ah,BYTE PTR [ebp+0xa]
<+8>: shl ax,0x10
<+12>: sub al,BYTE PTR [ebp+0xc]
<+15>: add ah,BYTE PTR [ebp+0xd]
<+18>: xor ax,WORD PTR [ebp+0x10]
<+22>: nop
<+23>: pop ebp
<+24>: ret
Stack
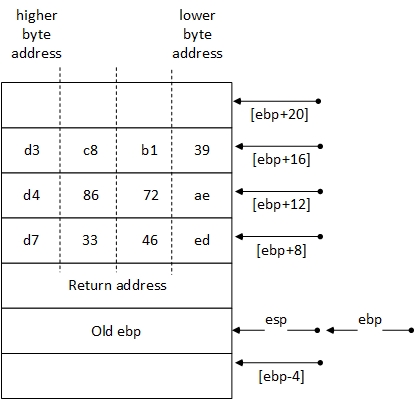
Solution
Step 1. xor eax,eax
eax is 0’d out.
Step 2. mov ah,BYTE PTR [ebp+0xa]
Most significant byte of AX -> ah = 0x33
Step 3. shl ax,0x10
Shift contents of AX left by 16 bits -> AX =0x0000
Step 4. sub al,BYTE PTR [ebp+0xc]
Least significant byte of AX -> al = 0x00 – 0xae = -0xae or 0x52 using two’s complement
-0xae: 1010 1110
2’s complement: 0101 0001 + 1
0x52: 0101 0010
Step 5. add ah,BYTE PTR [ebp+0xd]
Most significant byte of AX -> ah = 0x00 + 0x72 = 0x72
Step 6. xor ax,WORD PTR [ebp+0x10]
AX = 0x7252 xor 0xb139 = 0xc36b
0x7252: 0111 0010 0101 0010
xor 0xb139: 1011 0001 0011 1001
0xc36b: 1100 0011 0110 1011
