Reverse Engineering
Assembly code for a 32-bit linux binary provided with 2 calling arguments. The arguments are passed in the stack when using the x32 calling convention. Follow the program to get the result.
Function call: asm2(0x4,0x2d)
Assembly Code:
asm2:
<+0>: push ebp
<+1>: mov ebp,esp
<+3>: sub esp,0x10
<+6>: mov eax,DWORD PTR [ebp+0xc]
<+9>: mov DWORD PTR [ebp-0x4],eax
<+12>: mov eax,DWORD PTR [ebp+0x8]
<+15>: mov DWORD PTR [ebp-0x8],eax
<+18>: jmp 0x50c <asm2+31>
<+20>: add DWORD PTR [ebp-0x4],0x1
<+24>: add DWORD PTR [ebp-0x8],0xd1
<+31>: cmp DWORD PTR [ebp-0x8],0x5fa1
<+38>: jle 0x501 <asm2+20>
<+40>: mov eax,DWORD PTR [ebp-0x4]
<+43>: leave
<+44>: ret
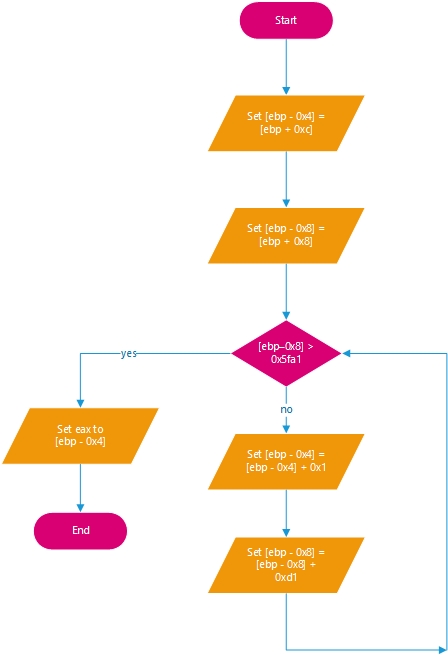
Flow Chart:
Stack:

Solution:
The program function is a counter.
- [ebp-0x4] is a counter that starts at a set value 0x2d and then increments by 1
- [ebp-0x8] is the variable that starts at 0x4 and is increased by 0xd1 until it exceeds 0x5fa1
